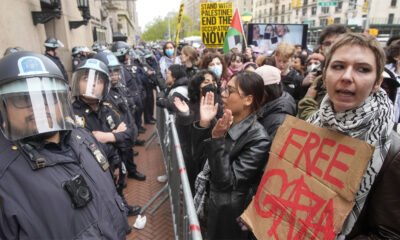International
Cyberattackers used US company RayoByte in efforts to crash media sites

THE cyberattack against the Somali Journalists Syndicate could not have come at a worse time. A distributed denial-of-service attack known by its acronym DDoS, flooded the local press freedom group’s website with traffic in early August and knocked it offline.
Days later, authorities arrested SJS staff member and Kaab TV editor Mohamed Ibrahim Osman Bulbul in connection with his reporting on alleged corruption. The tandem crises placed major strain on the organization.
“It was a very traumatic week. Sleepless. Very stressful. We could not publish our statement, the first statement of Mohamed’s detention,” SJS secretary general Abdalle Ahmed Mumin told CPJ in an interview from the U.K., where he fled earlier this year after he was repeatedly arrested by Somali authorities. “Imagine someone attacking your team, detaining one of your team, and you’re not able to communicate to the international world because your website has been taken down.”
SJS found some relief when it connected with Qurium, a Sweden-based nonprofit that began hosting SJS’s website. But a week after the initial attack, another DDoS flood hit the website. This time, Qurium was able to protect SJS from going offline. Qurium’s analysis of these additional attacks also found that a U.S. company, RayoByte, had provided the tools used in the attack.
Sprious, which owns RayoByte, told Qurium in an email, which CPJ reviewed, that it had “removed the abusive user” from its network and added the SJS site to its “blacklist” to prevent it from being targeted further.
SJS isn’t the only news outlet that has suffered a DDoS attack using RayoByte’s services. News outlets from at least five other countries — Kosovo, Nigeria, Kyrgyzstan, the Philippines, and Turkmenistan — have faced similar attacks over the last two years, according to Qurium’s analysis. These incidents provide a rare look at the mechanics of online censorship efforts and how private corporations can profit from them.
READ ALSO:
-
How Burna Boy, Olamide inspired my venture into music – Don Lamba
-
Harsh Economy: UNN cancels Post-UTME screening test
-
Internet fraudster forfeits $22,000, N500,000 as court jails him
Sprious declined CPJ’s requests for an interview and did not directly answer a list of written questions. But in emailed statements to CPJ, Sprious said it was “deeply concerned” about reports that its services were “allegedly” used in DDoS attacks. “We firmly stand against any form of online harassment or harm, including cyber-attacks, especially when it concerns entities that play a crucial role in promoting press freedom and the safety of journalists,” it said.
Headquartered in Lincoln, Nebraska, Rayobyte, formerly known as Blazing SEO, is one of many companies that sells clients access to Internet Protocol (IP) addresses, unique numbers assigned to internet-connected devices, for “scraping,” a method for extracting large amounts of data from websites. RayoByte’s website lists a range of prices for access to IP addresses based on variables including type and speed.
One way to conduct scraping is through repeated requests to visit a site with different IP addresses. Journalists and researchers use scraping as a reasearch technique, but when IP requests are directed quickly and en masse toward a specific site in order to overwhelm it and knock it offline, this constitutes a DDoS attack.
CPJ has documented DDoS attacks against outlets conducting critical journalism around the world. These cyberattacks also often take place alongside other threats to journalists’ safety and press freedom.
Qurium’s analysis shows that it blocked nearly 20,000 IP addresses from hitting the SJS website with millions of requests on August 18 and 19. The largest portion of the traffic (nearly 50%) came via RayoByte and its hosting partners, the analysis said. The second half of the traffic came through several other online channels, including virtual private networks (VPNs).
“We were very effective at mitigating the attack because within a few hours we realized we had seen this type of traffic before,” Qurium’s Lundström told CPJ. “We have met this [attacking] infrastructure in the past…this infrastructure is no joke.”
Similar DDoS attacks began almost immediately after Kosovo-based news site Nacionale began publishing in March 2022, covering local politics and social issues, co-founder Visar Arifaj told CPJ in a recent phone interview. “Our website would be down quite often. Because we were still fresh in the news market, it really had an impact for us to reach our audiences,” Arifaj said. “For us to be down a couple of hours during the day was a huge blow.”
Qurium began hosting and defending Nacionale in September 2022, and in March and April 2023 Qurium notified Sprious that attackers had been using its services against the outlet.
READ ALSO:
-
Why I slept with my husband’s younger brother, got pregnant for him – Housewife
-
BREAKING: PEPC Judgment: Peter Obi writes Obidients, supporters
-
Neymar breaks Pele’s Brazil goal-scoring record
In emails from March, Qurium informed Sprious of attacks lasting “several hours non-stop.” One of the attacks “sourced” millions of web requests from IP addresses “publicly advertised by Rayobyte/BlazingSEO,” Qurium said. Sprious responded that it had “blacklisted” access to Nacionale’s website and it had barred the “user” responsible – which Sprious did not name — from accessing its services, but in April Qurium again tracked a DDoS attack against Nacionale involving RayoByte. In response to Qurium’s email about the April attack, Sprious said it had “discovered an issue” with its “security controls,” and had addressed it “to prevent further traffic.”
However, RayoByte-sourced internet traffic to Nacionale’s website did not stop and featured in DDoS attacks against the outlet in July and August, Lundström told CPJ. While Kosovo police arrested and prosecuted one man in connection with the cyberattacks and Qurium has successfully prevented the continued attacks from taking Nacionale offline, Lundström told CPJ that incoming traffic shows attackers continuing to harness IPs from a combination of proxy services, VPNs, and other sources.
Alongside the cyberattacks, Nacionale’s staff have been subjected to “constant” online harassment for their work and were recently physically attacked on the job, though those attackers have been arrested, Arifaj told CPJ. “This constant pressure, even when it doesn’t get to the journalists physically and in a direct manner, you can see that it does a lot for their burnout,” he added. “It does take a toll, mentally, on everyone.”
Since 2022, Qurium has additionally tracked DDoS attacks with IPs sourced from RayoByte against four other outlets: Peoples Gazette from Nigeria, Kloop from Kyrgyzstan, Bulatlat from the Philippines, and Turkmen.news, which reports on Turkmenistan from exile. The attacks on three of the four outlets, excluding Kloop, also involved traffic via VPNs.
In its statements to CPJ, Sprious said it investigates reports of DDoS attacks using its services and takes “appropriate actions with the end user that we believe is responsible” and “steps to mitigate the reported issues, including, but not limited to, blacklisting associated domains and working diligently to remove abusive users.”
The statements did not respond directly to CPJ’s requests for details of the customers responsible for these attacks and how the company responded in each case.
Lundström told CPJ that Sprious has yet to respond to Qurium’s emails concerning the attacks on Peoples Gazette, Kloop, Bulatlat, and Turkmen.news, as well as the additional attacks on Nacionale in July and August.
Proxies and VPNs have valid and important uses for ensuring internet users, including journalists, can maintain privacy online. Rights organizations, including CPJ, recommend the use of VPNs to defend against surveillance; individuals can use it to avoid state-backed online censorship, and companies use them to safeguard proprietary information. But Lundström described the use of proxy and VPN services to conduct DDoS attacks as a “weaponization” of these tools. “You’re hiding in a tool [made] for another purpose,” he said of the attackers. “I think it’s a strategic decision.”
READ ALSO:
-
BREAKING: African Union joins G-20 as permanent member
-
Liverpool captain banned for another match, fined £100k
-
Police arrest man who allegedly shot his pregnant girlfriend in front of commuters
“DDoS attacks are illegal under a section of the [U.S.] Computer Fraud and Abuse Act,” Gabe Rottman, director of the Technology and Press Freedom Project at the U.S.-based Reporters Committee for Freedom of the Press, which provides legal support to journalists, told CPJ. But he said that it is not necessarily illegal for proxy or VPN companies’ to provide services that are then used in DDoS attacks.
That doesn’t mean service providers can’t take actions. “You can have technology providers doing appropriate things to protect their users and others at the same time as they build their service in a way that protects privacy,” Rottman said. “If … you become aware of bad actors doing bad things, notify the authorities, stop them from using your service, mitigate the damage.”
Attacks on the SJS website have continued, Lundström told CPJ, though none of the IPs have come via RayoByte since Qurium and CPJ contacted Sprious for comment. Nevertheless, Lundström wants RayoByte’s leadership to do more to address the fact that attackers have repeatedly come to the company’s services to target media sites. “[RayoByte’s] making all the money,” he said. “And we have to do all this extra work and build new infrastructure to deal with all this shit.”
As for SJS, Abdalle remains worried about his colleague, who is still behind bars. But he says he’s confident that the press freedom group’s website will remain accessible.
He still doesn’t know the identity of the person or people who launched the cyberattack, but he imagines what they might be thinking: “Now they are witnessing, they are coming into a new reality that even after the attack SJS is still resilient. SJS is still active. SJS is still available and is able to work and operate effectively both online and physically inside Somalia.”
Jonathan Rozen is CPJ’s senior Africa researcher. Previously, he worked in South Africa, Mozambique, and Canada with the Institute for Security Studies, assessing Mozambican peace-building processes. He also wrote analyses for the think tank adelphi on links between climate action and conflict prevention. Rozen was a U.N. correspondent for IPS News and has written for Al-Jazeera English and the International Peace Institute.
Cyberattackers used US company RayoByte in efforts to crash media sites
International
Tragic moose attack claims life of photographer in Homer, Alaska

Tragic moose attack claims life of photographer in Homer, Alaska
In a heartbreaking incident in Homer, Alaska, a 70-year-old man, Dale Chorman, was fatally attacked by a mother moose while attempting to photograph her newborn calves on Sunday. Chorman, accompanied by a friend, was walking through the brush searching for the moose and her offspring when the protective mother charged at them.
According to Alaska State Troopers, the moose kicked Chorman, who was pronounced dead at the scene. The incident occurred around 11:52 a.m., and by the time first responders arrived, the moose had already left the area. Chorman’s family has expressed a wish that the animal not be found, highlighting the tragic and natural aspect of the encounter.
READ ALSO:
- Insecurity: How to make state police effective, by Senate leader
- 78 suspected internet fraudsters arrested in Enugu, Imo
- Kano mosque attack: Principal suspect pleads guilty, remanded
This incident serves as a sobering reminder of the dangers of approaching wildlife, especially mothers with their young. Moose calving season, which runs from mid-May to mid-June, is a particularly sensitive period for these animals. Wildlife experts and authorities have long urged the public to maintain a safe distance from wildlife to avoid such tragic encounters.
Dale Chorman is remembered by his family as a loving husband, devoted father, and cherished friend, leaving behind a community that deeply mourns his loss. His death underscores the importance of respecting wildlife and the inherent risks of close encounters with these animals.
Tragic moose attack claims life of photographer in Homer, Alaska
International
Gaza conflict: Israel, Hamas reject ICC arrest warrant

Gaza conflict: Israel, Hamas reject ICC arrest warrant
Israel and Hamas have both vehemently rejected recent attempts to arrest their leaders for war crimes by the International Criminal Court (ICC) amidst ongoing heavy fighting in the Gaza Strip. The ICC’s prosecutor, Karim Khan, announced that he had sought arrest warrants for senior figures from both sides due to alleged war crimes in the current conflict.
The Israeli government condemned the move, with Prime Minister Benjamin Netanyahu and Defence Minister Yoav Gallant being specifically targeted for crimes including “willful killing,” “extermination and/or murder,” and “starvation.” Israel called the demands a “historical disgrace.”
On the other side, Hamas also denounced the ICC’s actions. The Palestinian militant group, with leaders such as Qatar-based Ismail Haniyeh and Gaza chief Yahya Sinwar named, faces accusations including “taking hostages,” “rape and other acts of sexual violence,” and “torture.”
READ ALSO:
- Anambra school where pupil was beaten to coma shut, teacher arrested
- BREAKING: Iranian Imam survived helicopter crash for an hour, tried to raise help – Report
- Student killed in Anambra seminary school fire
Khan asserted that international law and the laws of armed conflict apply to everyone, emphasizing that no one is immune from prosecution. Should the ICC judges approve the warrants, the 124 ICC member states would be obligated to arrest the listed leaders if they enter their territories, though the ICC lacks the means to enforce these warrants independently.
As the conflict persists, Israeli troops continue their operations in Rafah, targeting what they describe as the last Hamas stronghold, with Prime Minister Netanyahu reaffirming Israel’s commitment to dismantling Hamas and securing the release of all hostages. The UN reported that over 810,000 Palestinians have fled Rafah due to the intense fighting.
Gaza conflict: Israel, Hamas reject ICC arrest warrant
International
BREAKING: Iranian Imam survived helicopter crash for an hour, tried to raise help – Report

BREAKING: Iranian Imam survived helicopter crash for an hour, tried to raise help – Report
As more details emerge about the helicopter crash, a harrowing picture is taking shape.
One of the passengers on board was Mohammad Ali Al-Hashem, Friday Prayer Imam of Tabriz, the city the convoy was travelling to.
According to Mohammad Nami, head of Iran’s Crisis Management Agency, Al-Hashem survived for a whole hour after the crash. He even tried to make contact with the president’s office.
READ ALSO:
- JUST IN: South African highest court disqualifies Jacob Zuma from contesting election
- NSCDC uncovers fresh illegal refining sites in Rivers
- Ekiti selected monarch arraigned for certificate forgery
“No DNA tests were needed to identify the passengers,” says Nami. In total, nine people including the flight crew were killed in the helicopter crash.
BREAKING: Iranian Imam survived helicopter crash for an hour, tried to raise help – Report
-

 Sports2 days ago
Sports2 days agoFlamingos thrash Burkinabe Girls 6-0 in U-17 World Cup qualifier
-

 News3 days ago
News3 days agoNigeria will stop fuel importation by June – Dangote
-

 Africa2 days ago
Africa2 days agoArmy foils coup to topple DR Congo president
-

 metro1 day ago
metro1 day agoHealth worker stabbed to death in Minna
-

 metro3 days ago
metro3 days agoUpdated: Many injured, shops destroyed in truck, BRT bus crash on Lagos-Ibadan Expressway (PHOTOS)
-

 metro3 days ago
metro3 days agoBreaking: Women protest against return of armed Okuama youths (+ Photos)
-

 Education2 days ago
Education2 days agoWigwe varsity becomes most expensive Nigerian university, unseats Nile, Baze
-

 International2 days ago
International2 days agoJUST IN: Helicopter carrying Iran’s president crash-lands